编程 tips
Task estimation
- the complexity of the task
- the associated dependencies / possible side effects
- the own experience (e.g., when I had to implement something that I had never done before)
- uncertainty / not completely precise requirements
- existing legacy code
- other technical difficulties / dependencies in the code
加密 cryptography
-
Hashing: SHA-512
用于密码校验等
-
Symmetric encryption: AES-256
对称加密,更方便快捷,但需要分享单一的密钥,无法识别加密者
-
Asymmetric encryption: RSA-2048
不对称加密,保留私钥,分享公钥,可以识别加密者。但更麻烦费时
Screenshot from command line
- https://stackoverflow.com/questions/67714554/creating-macro-to-take-and-save-screenshot-and-paste-saved-location-into-clipboa?noredirect=1#comment119710754_67714554
- https://superuser.com/questions/75614/take-a-screen-shot-from-command-line-in-windows
- https://stackoverflow.com/questions/17435995/paste-an-image-on-clipboard-to-emacs-org-mode-file-without-saving-it
CodeQL
QL is a code analysis engine for security teams to automate variant analysis for product security. Quickly find variants of all vulnerabilities in your code.
Bing query parameters
search engine - What query parameters does Bing have? - Web Applications Stack Exchange
https://www.bing.com/search?q=hello&count=1
q # search keywords
count # how many results per page
adlt # safe search (strict, moderate, off)
cc # ISO 3166 country code
setlang # set interface language, e.g. fr-fr, en-us
lf=1 # pages only in the same language as the interface
format=rss # get result page as RSS
Approximate timing for various operations on a typical PC
execute typical instruction 1/1,000,000,000 sec = 1 nanosec
fetch from L1 cache memory 0.5 nanosec
branch misprediction 5 nanosec
fetch from L2 cache memory 7 nanosec
Mutex lock/unlock 25 nanosec
fetch from main memory 100 nanosec
send 2K bytes over 1Gbps network 20,000 nanosec
read 1MB sequentially from memory 250,000 nanosec
fetch from new disk location (seek) 8,000,000 nanosec
read 1MB sequentially from disk 20,000,000 nanosec
send packet US to Europe and back 150 milliseconds = 150,000,000 nanosec
books about software engineering history
What are the books about software engineering history that you have enjoyed most?
- Masters of Doom: The awesome history about ID Software and the making of Doom.
- The Making of Prince of Persia: Journals 1985 - 1993: A history about the iconic game and its author, Jordan Mechner
- Making it Big in Software: A set of essays and interviews to software legends.
Code browsing
Data Representation
A Tutorial on Data Representation - Integers, Floating-point numbers, and characters
The IEEE Standard for Floating-Point Arithmetic (IEEE 754)
Integer number 1, floating-point number 1.0, character symbol '1' and string "1" are totally different inside the computer memory. You need to know the difference to write good and high-performance programs.
- In 8-bit signed integer, integer number
1is represented as00000001B. - In 8-bit unsigned integer, integer number
1is represented as00000001B. - In 16-bit signed integer, integer number
1is represented as00000000 00000001B. - In 32-bit signed integer, integer number
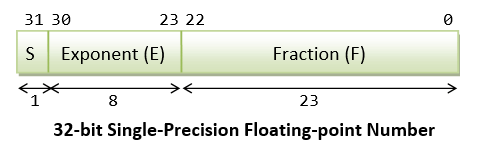
1is represented as00000000 00000000 00000000 00000001B. - In 32-bit floating-point representation, number
1.0is represented as0 01111111 0000000 00000000 00000000, i.e., S=0, E=127, F=0.
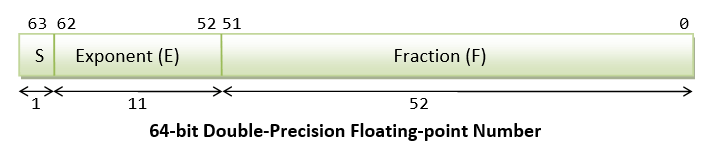
- In 64-bit floating-point representation, number
1.0is represented as0 01111111111 0000 00000000 00000000 00000000 00000000 00000000 00000001B, i.e., S=0, E=1023, F=0
- In 8-bit Latin-1, the character symbol
'1'is represented as00110001B(or31H). - In 16-bit UCS-2, the character symbol
'1'is represented as00000000 00110001B. - In UTF-8, the character symbol
'1'is represented as00110001B.
不同编码规范下 unicode 文本的编码
UCS-2: 0048 0069 002C 60A8 597D 0021 [16-bit fixed-length]
H i , 您 好 !
US-ASCII: 48 69 2C 3F 3F 21 [8-bit fixed-length]
H i , ? ? !
ISO-8859-1: 48 69 2C 3F 3F 21 [8-bit fixed-length]
H i , ? ? !
UTF-8: 48 69 2C E6 82 A8 E5 A5 BD 21 [1-4 bytes variable-length]
H i , 您 好 !
UTF-16: FE FF 00 48 00 69 00 2C 60 A8 59 7D 00 21 [2-4 bytes variable-length]
BOM H i , 您 好 ! [Byte-Order-Mark indicates Big-Endian]
UTF-16BE: 00 48 00 69 00 2C 60 A8 59 7D 00 21 [2-4 bytes variable-length]
H i , 您 好 !
UTF-16LE: 48 00 69 00 2C 00 A8 60 7D 59 21 00 [2-4 bytes variable-length]
H i , 您 好 !
GBK: 48 69 2C C4 FA BA C3 21 [1-2 bytes variable-length]
H i , 您 好 !
Big5: 48 69 2C B1 7A A6 6E 21 [1-2 bytes variable-length]
H i , 您 好 !
算法练习
加载远程文件系统到本地
How To Use SSHFS to Mount Remote File Systems Over SSH
Tail call
Tail call (尾调用):一个函数调用是函数中的最后一个语句,且该调用会产生相同的调用过程。则称这个函数调用为 tail-recursive(尾递归)。